文章目录:
-
基本论文结构
-
算法
-
图片
-
表格
-
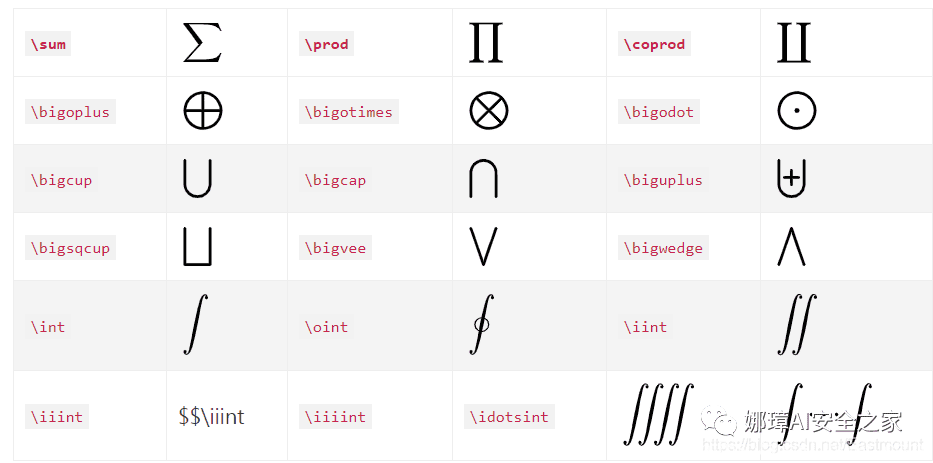
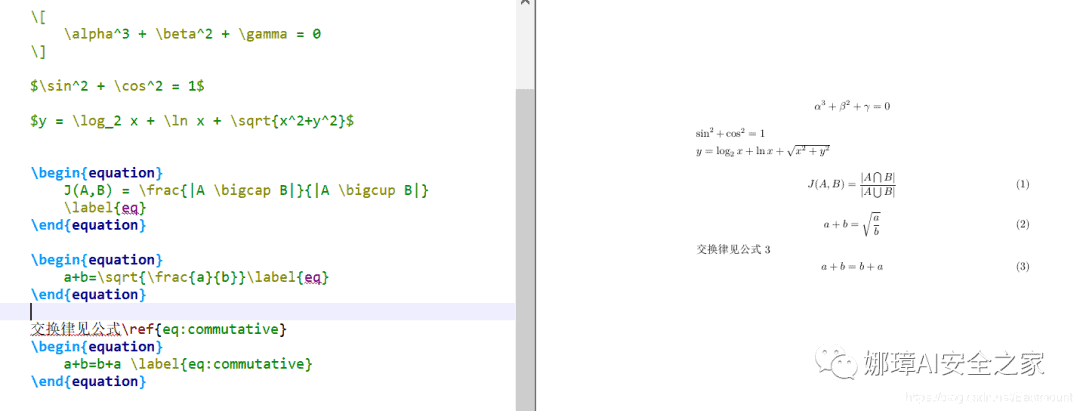
公式
-
特殊符号
-
参考文献
-
序号
-
总结
基本论文结构
什么是LaTeX
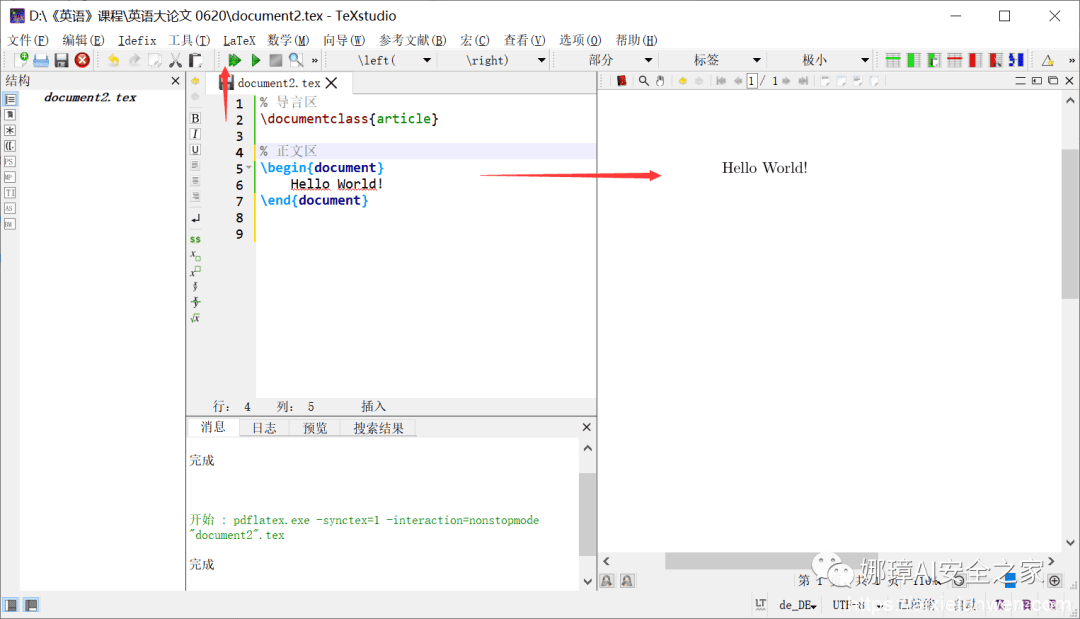
基本结构
% 导言区documentclass{article}title{My First Document}author{Eastmount}date{today}% 正文区begin{document}maketitleHello World!end{document}
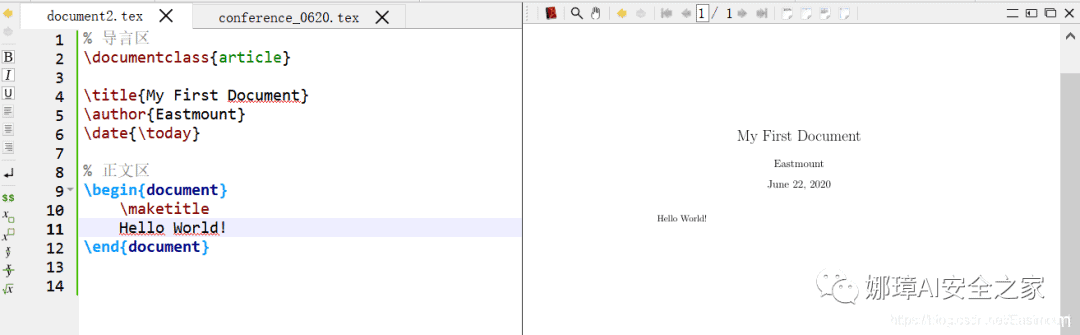
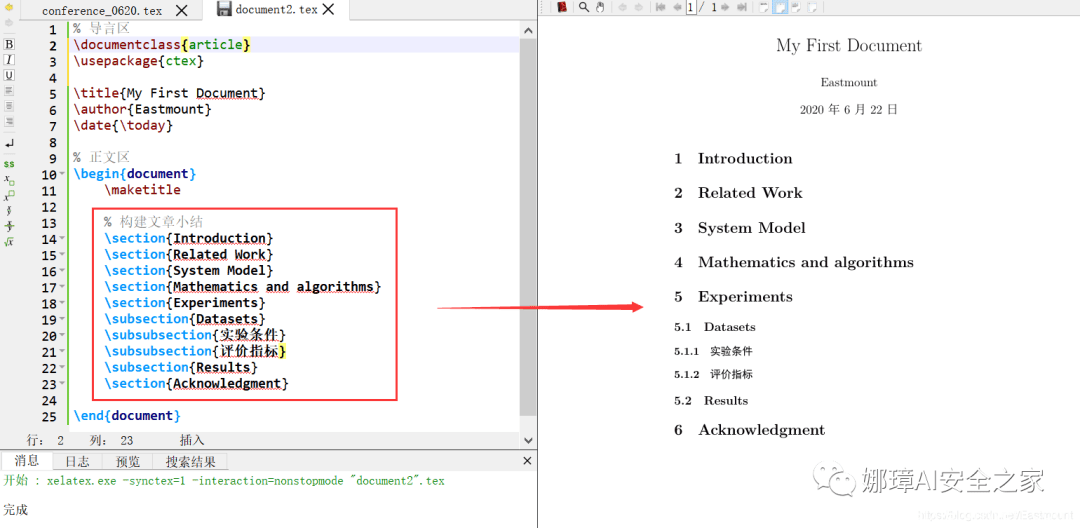
篇章结构
导言区documentclass{article}usepackage{ctex}title{My First Document}author{Eastmount}date{today}% 正文区begin{document}maketitle构建文章小结section{Introduction}section{Related Work}section{System Model}section{Mathematics and algorithms}section{Experiments}subsection{Datasets}subsubsection{实验条件}subsubsection{评价指标}subsection{Results}section{Acknowledgment}end{document}
算法
algorithm
usepackage{algorithm}usepackage{algorithmic}
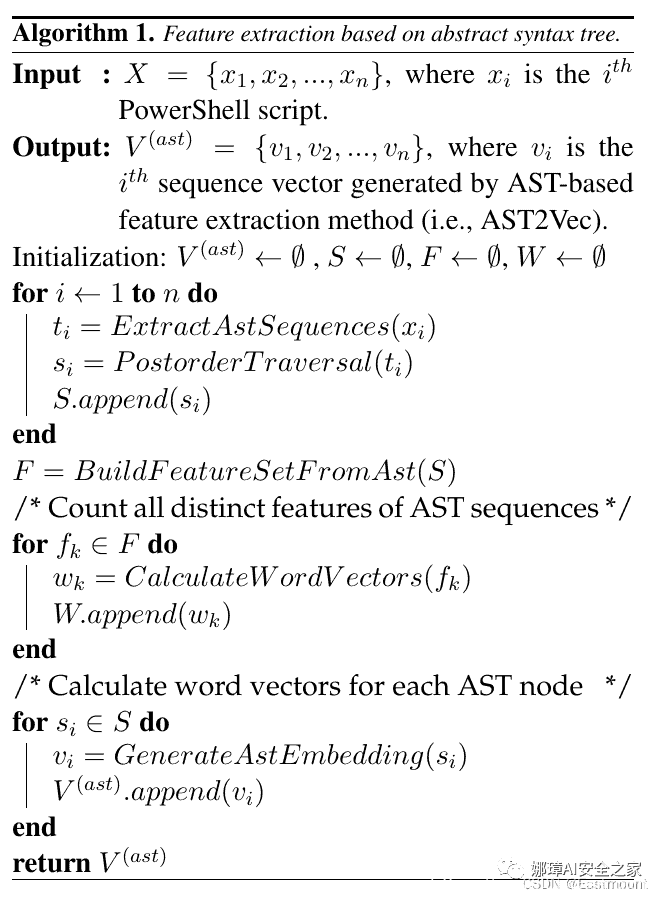
begin{algorithm}[!ht]caption{Feature extraction based on abstract syntax tree.}begin{algorithmic}[1]REQUIRE {$X=left{x_1,x_2,...,x_nright}$, where $x_i$ is the $i^{th}$ PowerShell script.}ENSURE {$V^{(ast)}=left{v_1,v_2,...,v_nright}$, where $v_i$ is the $i^{th}$ sequence vector generated by AST-based feature extraction method (i.e., AST2Vec).}STATE $V^{(ast)} leftarrow emptyset$ , $S leftarrow emptyset$, $F leftarrow emptyset$, $W leftarrow emptyset$FOR{$i leftarrow 1$ {bf to} $n$}STATE $t_i = ExtractAstSequences( x_i )$STATE $s_i = PostorderTraversal( t_i )$STATE $S.append( s_i )$ENDFORSTATE $F = BuildFeatureSetFromAst(S) $STATE $//$ Count all distinct features of AST sequences.FOR{each $f_k in F$}STATE $w_k = CalculateWordVectors( f_k )$STATE $W.append( w_k )$ENDFORSTATE $//$ Calculate word vectors for each AST node.FOR{each $s_i in S$}STATE $v_i = GenerateAstEmbedding( s_i )$STATE $V^{(ast)}.append( v_i )$ENDFORSTATE {bf return} {$V^{(ast)}$}end{algorithmic}label{algorithm1}end{algorithm}
algorithm2e
usepackage{algorithm}usepackage[algo2e]{algorithm2e}
begin{algorithm}[!ht]caption{Feature extraction based on abstract syntax tree.}label{algorithm1}SetAlgoLinedSetKwInOut{Input}{Input}SetKwInOut{Output}{Output}Input{$X=left{x_1,x_2,...,x_nright}$, where $x_i$ is the $i^{th}$ PowerShell script.}Output{$V^{(ast)}=left{v_1,v_2,...,v_nright}$, where $v_i$ is the $i^{th}$ sequence vector generated by AST-based feature extraction method (i.e., AST2Vec).}Initialization: $V^{(ast)} leftarrow emptyset$ , $S leftarrow emptyset$, $F leftarrow emptyset$, $W leftarrow emptyset$For{$i leftarrow 1$ KwTo $n$}{$t_i = ExtractAstSequences( x_i )$$s_i = PostorderTraversal( t_i )$$S.append( s_i )$}$F = BuildFeatureSetFromAst(S) $tcc{Count all distinct features of AST sequences}For{$f_k in F$}{$w_k = CalculateWordVectors( f_k )$$W.append( w_k )$}tcc{Calculate word vectors for each AST node}For{$s_i in S$}{$v_i = GenerateAstEmbedding( s_i )$$V^{(ast)}.append( v_i )$}Return{$V^{(ast)}$}end{algorithm}
图片
基本用法
导言区documentclass{article}usepackage{ctex}usepackage{graphicx}% 指定图片在当前目录下figures目录下graphicspath{{figures/}}% 正文区begin{document}插入图片includegraphics{fig1}缩放比例includegraphics[scale=0.5]{fig1}固定图像高度includegraphics[height=2cm]{fig1.png}固定图像宽度includegraphics[width=2cm]{fig1.png}图像高度和宽度基于includegraphics[height=0.2textheight]{fig1.png}includegraphics[width=0.2textwidth]{fig1.png}指定多个参数includegraphics[angle=-45,width=0.5textwidth]{fig1.png}end{document}
双栏显示
usepackage{stfloats}begin{figure*}[ht]centeringincludegraphics[width=0.8textwidth]{4.eps}caption{BER performance of original OFDM system and different companding schemes over AWGN channel (QPSK).}label{fig8}end{figure*}
h——放置在此处t——放置在顶部b——放置在底部p——浮动放置*——两栏放置
双图显示
begin{figure*}begin{minipage}[t]{0.48linewidth}centeringincludegraphics[scale=0.30]{Figure-7.eps}caption{The loss curve of different models.}label{fig7}end{minipage}begin{minipage}[t]{0.48linewidth}centeringincludegraphics[scale=0.30]{Figure-8.eps}caption{The accuracy curve of different models.}label{fig8}end{minipage}end{figure*}
usepackage{caption}usepackage{subfigure}begin{figure}[htbp]centering %居中subfigure[name of the first figure] %第一张子图{begin{minipage}[t]{0.4textwidth}centeringincludegraphics[scale=0.15]{fig2}end{minipage}}subfigure[name of the second figure] %第二张子图{begin{minipage}[t]{0.4textwidth}centeringincludegraphics[scale=0.2]{fig3}end{minipage}}caption{name of the figure} %大图名称label{fig-1} %图片引用标记end{figure}
begin{figure}[!hb]centeringsubfloat[label{fig:arm1}$Q^{*}$ values for arm 1]{includegraphics[width=.5linewidth]{1.eps}}%subfloat[label{fig:arm2}$Q^{*}$ values for arm 2]{includegraphics[width=.5linewidth]{1.eps}}\subfloat[label{fig:arm3}$Q^{*}$ values for arm 3]{includegraphics[width=.8linewidth]{1.eps}}caption{$Q^{*}$ values for different arms.}label{fig:arms}end{figure}
表格
基本用法
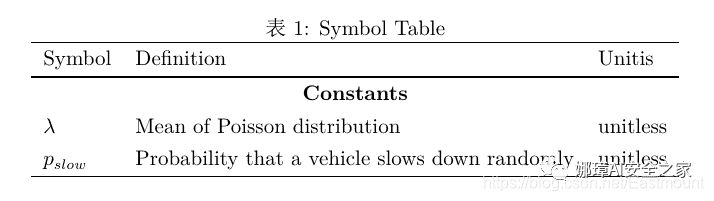
begin{table}caption{Symbol Table}centeringbegin{tabular}{lll}hlineSymbol & Definition & Unitis\noalign{globalarrayrulewidth1pt}hlinenoalign{globalarrayrulewidth0.4pt}multicolumn{3}{c}{textbf{Constants}}\$lambda$ & Mean of Poisson distribution & unitless\$p_{slow}$ & Probability that a vehicle slows down randomly & unitless\hlineend{tabular}end{table}
含注释的表格
usepackage{threeparttable}usepackage{float}usepackage{bbding}usepackage{pifont}
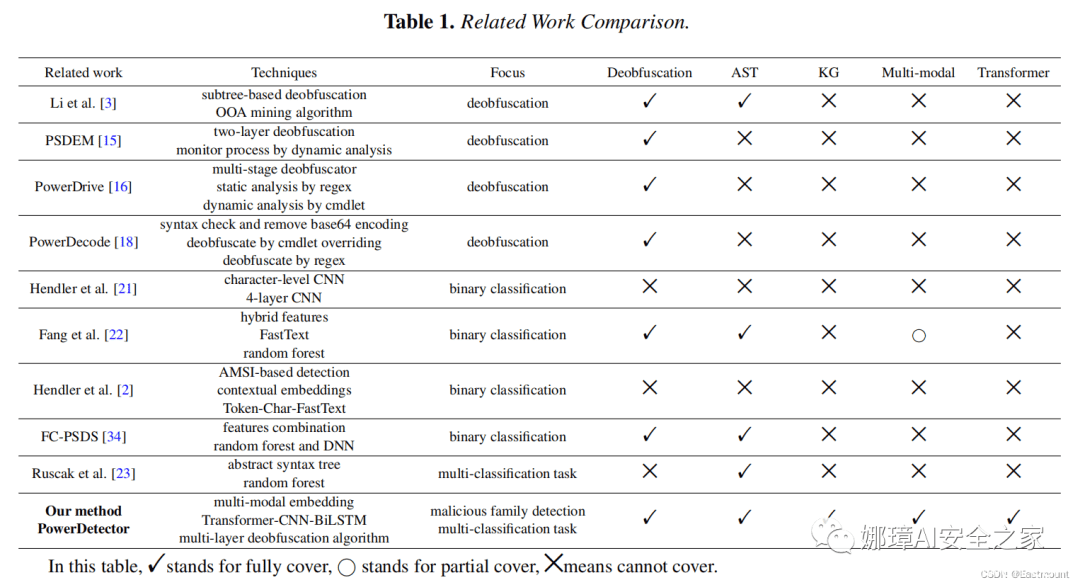
begin{table*}[!ht]centeringcaption{Related work comparison.}begin{threeparttable}resizebox{textwidth}{!}{begin{tabular}{ccccm{1.2cm}<{centering}m{1.2cm}<{centering}cc}hlineRelated work & Techniques & Focus & Deobfuscation & AST & KG & Multi-modal & Transformer \hlineLi et al. cite{b3} & makecell[c]{subtree-based deobfuscation \ OOA mining algorithm} & deobfuscation & Checkmark & Checkmark & XSolid & XSolid & XSolid \hlinePSDEM cite{b12} & makecell[c]{two-layer deobfuscation \ monitor process by dynamic analysis} & deobfuscation & Checkmark & XSolid & XSolid & XSolid & XSolid \hlinePowerDrive cite{b13} & makecell[c]{multi-stage deobfuscator \ static analysis by regex \ dynamic analysis by cmdlet} & deobfuscation & Checkmark & XSolid & XSolid & XSolid & XSolid \hlinePowerDecode cite{b15} & makecell[c]{syntax check and remove base64 encoding \ deobfuscate by cmdlet overriding \ deobfuscate by regex} & deobfuscation & Checkmark & XSolid & XSolid & XSolid & XSolid \hlineHendler et al. cite{b18} & makecell[c]{character-level CNN \ 4-layer CNN} & binary classification & XSolid & XSolid & XSolid & XSolid & XSolid \hlineFang et al. cite{b19} & makecell[c]{hybrid features \ FastText \ random forest} & binary classification & Checkmark & Checkmark & XSolid & $bigcirc$ & XSolid \hlineHendler et al. cite{b2} & makecell[c]{AMSI-based detection \ contextual embeddings \ Token-Char-FastText} & binary classification & XSolid & XSolid & XSolid & XSolid & XSolid \hlineFC-PSDS cite{b25} & makecell[c]{ features combination \ random forest and DNN} & binary classification & Checkmark & Checkmark & XSolid & XSolid & XSolid \hlineRuscak et al. cite{b20} & makecell[c]{abstract syntax tree \ random forest} & multi-classification task & XSolid & Checkmark & XSolid & XSolid & XSolid \hlinemakecell[c]{textbf{Our method} \ textbf{PowerDetector}} & makecell[c]{multi-modal embedding \ Transformer-CNN-BiLSTM \ multi-layer deobfuscation algorithm } & makecell[c]{malicious family detection \ multi-classification task} & Checkmark & Checkmark & Checkmark & Checkmark & Checkmark \hlineend{tabular}}begin{tablenotes}footnotesizeitem In this table, Checkmark stands for fully cover, $bigcirc$ stands for partial cover, XSolid means cannot cover.end{tablenotes}end{threeparttable}label{tab1}end{table*}
复杂表格合并multirow
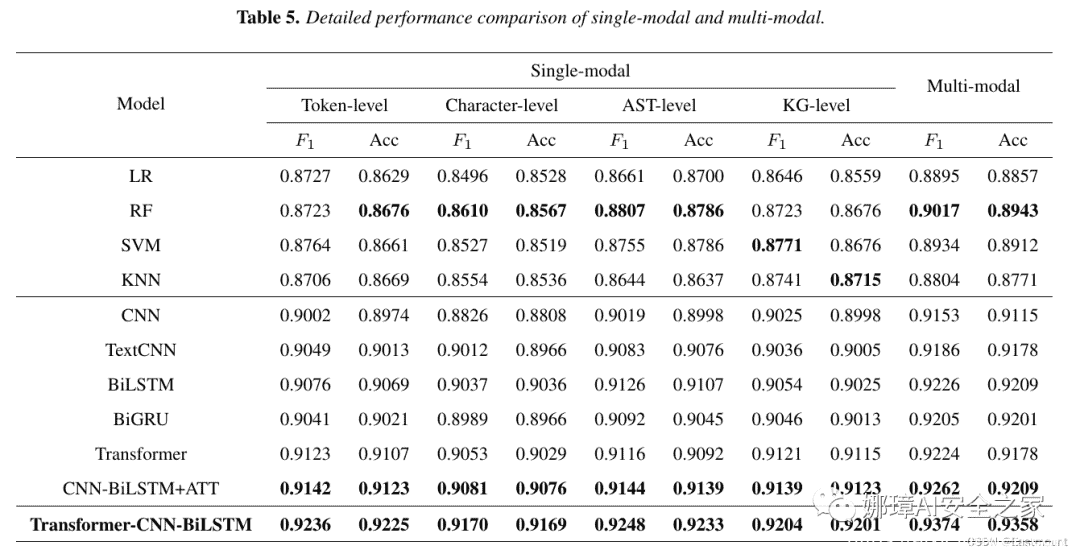
usepackage{multirow}begin{table*}[!ht]centeringcaption{Detailed performance comparison of single-modal and multi-modal.}resizebox{textwidth}{!}{begin{tabular}{ccccccccccc}hlinemultirow{3}{*}{Model} & multicolumn{8}{c}{Single-modal} & multicolumn{2}{c}{multirow{2}{*}{Multi-modal}} \cline{2-9}& multicolumn{2}{c}{Token-level} & multicolumn{2}{c}{Character-level} & multicolumn{2}{c}{AST-level} &multicolumn{2}{c}{KG-level} & multicolumn{2}{c}{} \cline{2-11}& $F_1$ & Acc & $F_1$ & Acc & $F_1$ & Acc & $F_1$ & Acc & $F_1$ & Acc \hlineLR & 0.8727 & 0.8629 & 0.8496 & 0.8528 & 0.8661 & 0.8700 & 0.8646 & 0.8559 & 0.8895 & 0.8857 \RF & 0.8723 & textbf{0.8676} & textbf{0.8610} & textbf{0.8567} & textbf{0.8807} & textbf{0.8786} & 0.8723 & 0.8676 & textbf{0.9017} & textbf{0.8943} \SVM & 0.8764 & 0.8661 & 0.8527 & 0.8519 & 0.8755 & 0.8786 & textbf{0.8771} & 0.8676 & 0.8934 & 0.8912 \KNN & 0.8706 & 0.8669 & 0.8554 & 0.8536 & 0.8644 & 0.8637 & 0.8741 & textbf{0.8715} & 0.8804 & 0.8771 \hlineCNN & 0.9002 & 0.8974 & 0.8826 & 0.8808 & 0.9019 & 0.8998 & 0.9025 & 0.8998 & 0.9153 & 0.9115 \TextCNN & 0.9049 & 0.9013 & 0.9012 & 0.8966 & 0.9083 & 0.9076 & 0.9036 & 0.9005 & 0.9186 & 0.9178 \BiLSTM & 0.9076 & 0.9069 & 0.9037 & 0.9036 & 0.9126 & 0.9107 & 0.9054 & 0.9025 & 0.9226 & 0.9209 \BiGRU & 0.9041 & 0.9021 & 0.8989 & 0.8966 & 0.9092 & 0.9045 & 0.9046 & 0.9013 & 0.9205 & 0.9201 \Transformer & 0.9123 & 0.9107 & 0.9053 & 0.9029 & 0.9116 & 0.9092 & 0.9121 & 0.9115 & 0.9224 & 0.9178 \CNN-BiLSTM+ATT & textbf{0.9142} & textbf{0.9123} & textbf{0.9081} & textbf{0.9076} & textbf{0.9144} & textbf{0.9139} & textbf{0.9139} & textbf{0.9123} & textbf{0.9262} & textbf{0.9209} \hlinetextbf{Our Method} & textbf{0.9236} & textbf{0.9225} & textbf{0.9170} & textbf{0.9169} & textbf{0.9248} & textbf{0.9233} & textbf{0.9204} & textbf{0.9201} & textbf{0.9374} &textbf{0.9358} \hlineend{tabular}}label{tab5}end{table*}
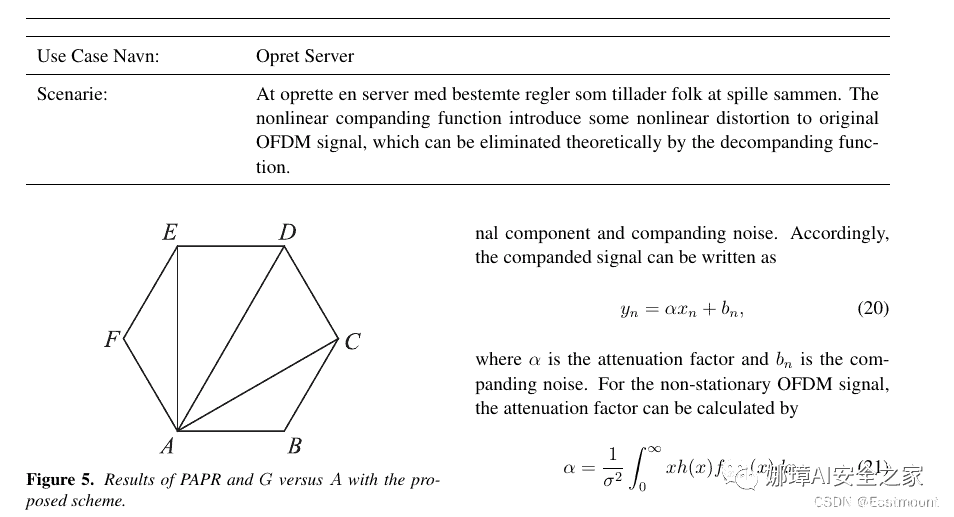
解决自动换行
begin{table*}[h]centeringbegin{tabular}{cc} hlineUse Case Navn: & Opret Server \hlineScenarie: & At oprette en server med bestemte regler som tillader folk at spille sammen.The nonlinear companding function introduce some nonlinear distortion to original OFDM signal,which can be eliminated theoretically by the decompanding function. \hlineend{tabular}label{tab5}end{table*}
usepackage{tabularx}begin{table*}[h]centeringbegin{tabularx}{textwidth}{p{4cm} X} hlineUse Case Navn: & Opret Server \hlineScenarie: & At oprette en server med bestemte regler som tillader folk at spille sammen.The nonlinear companding function introduce some nonlinear distortion to original OFDM signal,which can be eliminated theoretically by the decompanding function. \hlineend{tabularx}label{tab5}end{table*}
公式
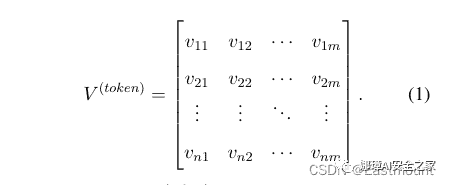
begin{equation}begin{aligned}V^{(token)}=begin{bmatrix}v_{11} & v_{12} & cdots & v_{1m} \v_{21} & v_{22} & cdots & v_{2m} \vdots & vdots & ddots & vdots \v_{n1} & v_{n2} & cdots & v_{nm} \end{bmatrix}end{aligned}label{eq1}end{equation}
begin{equation}begin{aligned}TokenPairs[j][k] =begin{cases}v_{jk} + 1 & exists <f_j,f_k> \v_{jk} + 0 & other \end{cases}.end{aligned}label{eq2}end{equation}
begin{equation}begin{aligned}Attention(textbf{Q},textbf{K},textbf{V}) = softmax left( frac{textbf{Q}textbf{K}^T}{sqrt{d_k}} right) textbf{V}.end{aligned}label{eq5}end{equation}
begin{equation}begin{aligned}Accuracy = sum_{i=1}^N Accuracy_i times w_i .end{aligned}label{eq15}end{equation}
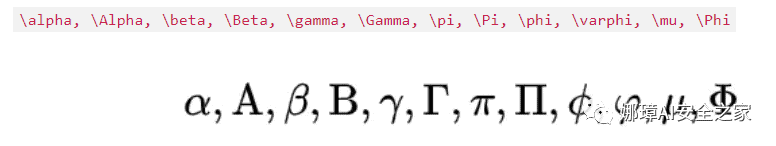
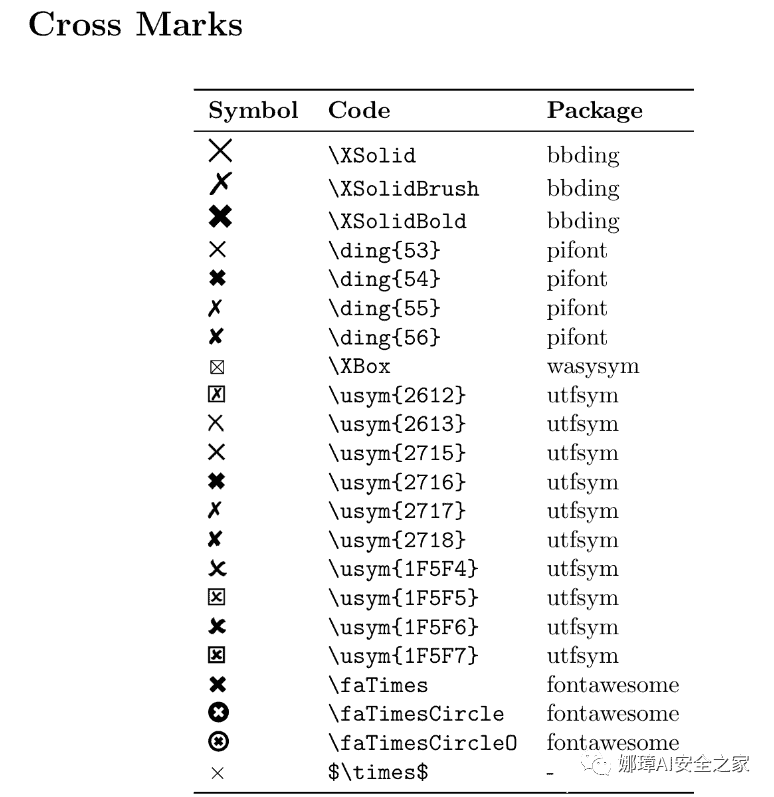
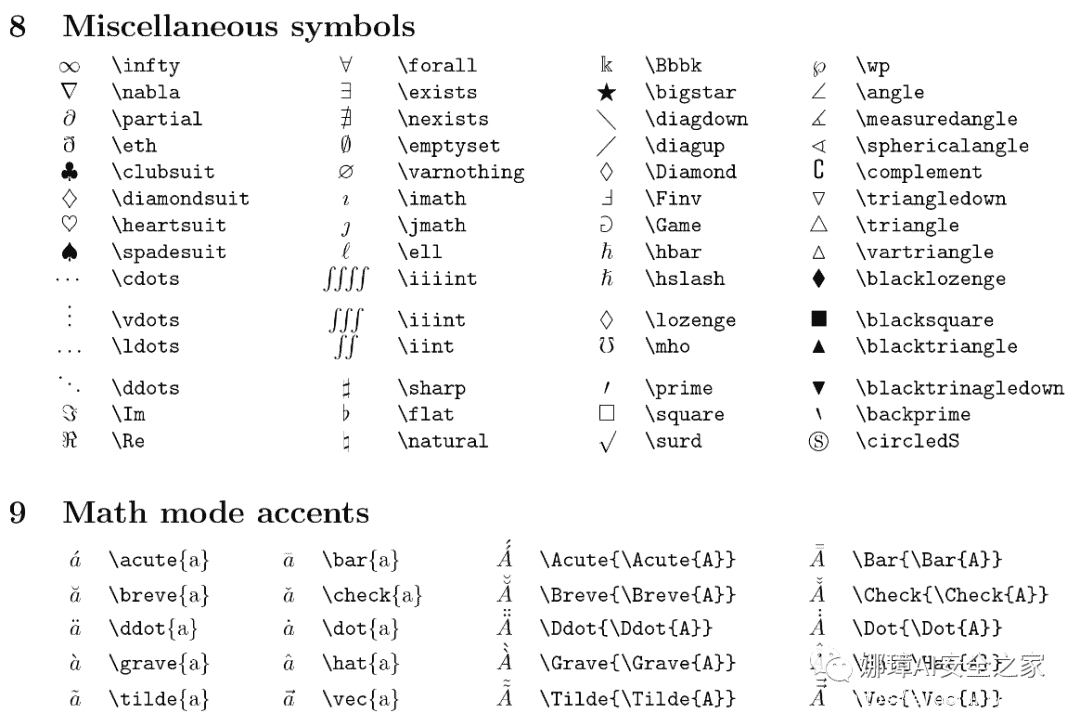
特殊符号
圆圈数字
usepackage{pifont}ding{184}
ding{182}ding{183}ding{184}ding{185}ding{186}ding{187}ding{188}ding{189}ding{190}ding{191}\ding{192}ding{193}ding{194}ding{195}ding{196}ding{197}ding{198}ding{199}ding{200}ding{201}\ding{202}ding{203}ding{204}ding{205}ding{206}ding{207}ding{208}ding{209}ding{210}ding{211}\
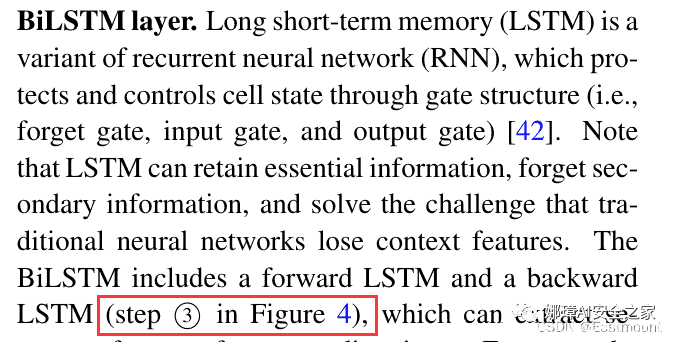
textcircled{3}$normalsize{textcircled{scriptsize{3}}}normalsizeenspace半圆
usepackage{tikz}newcommand*emptycirc[1][1ex]{tikzdraw (0,0) circle (#1);}newcommand*halfcirc[1][1ex]{%begin{tikzpicture}draw[fill] (0,0)-- (90:#1) arc (90:270:#1) -- cycle ;draw (0,0) circle (#1);end{tikzpicture}}newcommand*fullcirc[1][1ex]{tikzfill (0,0) circle (#1);}
fullcirchalfcircemptycirc
勾叉
usepackage{pifont} % ding{xx}usepackage{bbding} % Checkmark,XSolid,... (需要和pifont宏包共同使用)
checkmarkCheckmarkCheckmarkBoldXSolidXSolidBoldXSolidBrush
纸牌
$clubsuit$$spadesuit$$heartsuit$$diamondsuit$
参考文献
begin{thebibliography}{99}bibitem{ref1}Zheng L, Wang S, Tian L, et al., Query-adaptive late fusion for image search and person re-identification, Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, 2015: 1741-1750.bibitem{ref2}Arandjelović R, Zisserman A, Three things everyone should know to improve object retrieval, Computer Vision and Pattern Recognition (CVPR), 2012 IEEE Conference on, IEEE, 2012: 2911-2918.bibitem{ref3}Lowe D G. Distinctive image features from scale-invariant keypoints, International journal of computer vision, 2004, 60(2): 91-110.bibitem{ref4}Philbin J, Chum O, Isard M, et al. Lost in quantization: Improving particular object retrieval in large scale image databases, Computer Vision and Pattern Recognition, 2008. CVPR 2008, IEEE Conference on, IEEE, 2008: 1-8.end{thebibliography}
begin{thebibliography}{49}bibitem{b1} Microsoft, ``What is PowerShell? - PowerShell | Microsoft Docs,''Website: https://docs.microsoft.com/en-us/powershell/scripting/overview, 2022.bibitem{b2} D. Hendler, S. Kels, et al., ``AMSI-Based Detection of Malicious PowerShellCode Using Contextual Embeddings,'' in 15th ACM Asia Conference on Computer andCommunications Security (AsiaCCS). ACM, 2020, pp. 679-693.bibitem{b49} M. Ring, D. Schlor, et al., ``Malware detection on windows audit logs usingLSTMs,'' Computers & Security, vol.109, 2021, p. 102389.end{thebibliography}
@misc{b1,title = {What is PowerShell? - PowerShell | Microsoft Docs},url = {https://docs.microsoft.com/en-us/powershell/scripting/overview},author = {Microsoft},year = {2022}}@inproceedings{b2,title={Amsi-based detection of malicious powershell code using contextual embeddings},author={Hendler, Danny and Kels, Shay and Rubin, Amir},booktitle={Proceedings of the 15th ACM Asia Conference on Computer and Communications Security (AsiaCCS)},pages={679--693},year={2020},organization = {ACM}}@article{b49,title={Malware detection on windows audit logs using LSTMs},author={Ring, Markus and Schl{"o}r, Daniel and Wunderlich, Sarah and Landes, Dieter and Hotho, Andreas},journal={Computers & Security},volume={109},pages={102389},year={2021},publisher={Elsevier}}
序号
begin{itemize}item Every sentence should make sense.item There is a lot to be said.item Eschew the highfalutin.end{itemize}
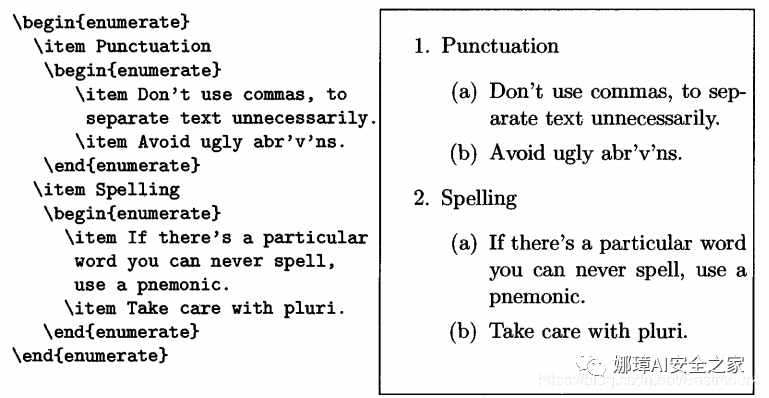
begin{enumerate}item Every sentence should make sense.item There is a lot to be said.item Eschew the highfalutin.end{enumerate}
begin{description}item[Rule 1.] Every sentence should make sense.item[Rule 2.] There is a lot to be said.item[Rule 3.] Eschew the highfalutin.end{description}
 ai论文写作
ai论文写作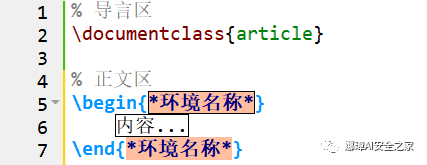

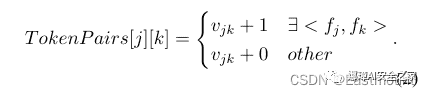
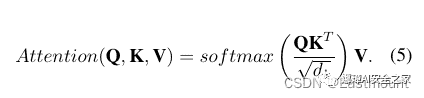
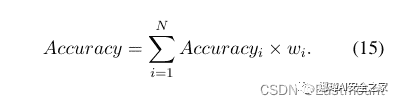

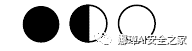
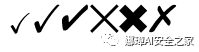
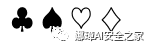










评论前必须登录!
立即登录 注册